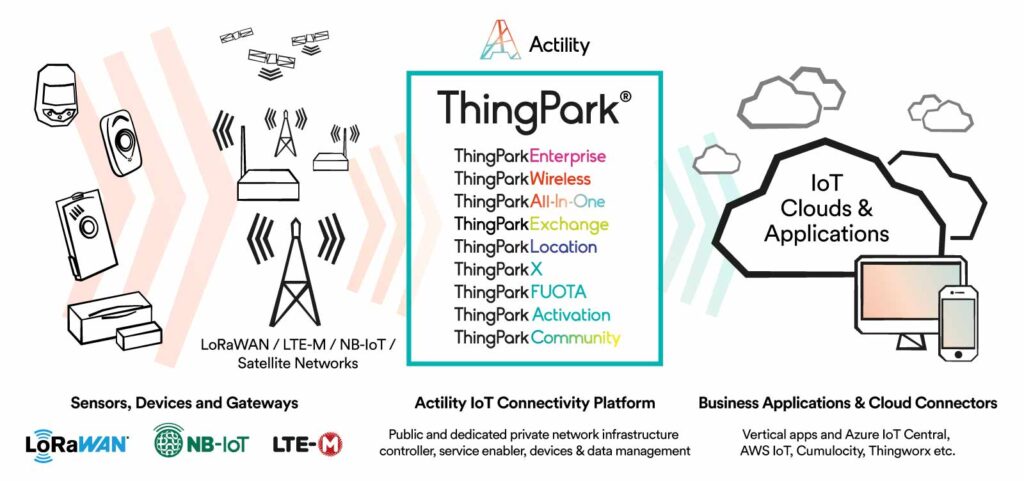
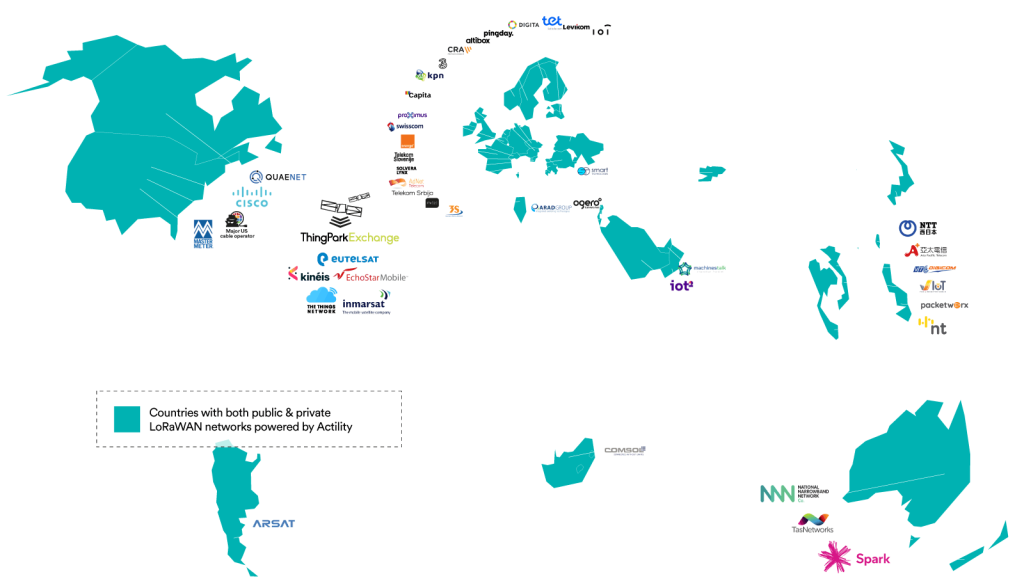
Network Architecture & Scalability
- Geo-redundant architecture, supporting Disaster Recovery Plan
- Fully horizontally-scalable multi-cluster core network architecture, each cluster supports up to 150K messages per second (1.2 billion devices), 500K macro gateways and up to 10 million pico/nano gateways.
- Multi-tenancy
- Fully horizontally-scalable back-office architecture
- Support of heterogeneous network deployments with seamless connectivity across a mix of macro and pico/nano gateways and optimized traffic routing algorithms
- Possibility to filter unwanted traffic at base station level to optimize backhaul resources
Connectivity & Backhaul
- Several backhaul options between gateway and core network: ethernet, cellular, satellite, WiFi...
- Several tunneling options between base stations and core network: IPSec and TLS.
- HTTPS for tunneling interface between the core network and application servers, including security signatures (token-based).
- Passive roaming, compliant with the latest official LoRaWAN Backend interfaces specification
- Support of all the LoRaWAN ISM bands: Europe and ETSI-compliant countries (EU863-870 and EU433), USA and Americas (US902-928), China (CN779-787 and CN470-510), Oceania and Americas
- (AU915-928), Asian Cluster (AS923), Korea (KR920-923), India (IN865-867) and Russia (RU864-870).
- Off-the-shelf regional profiles supported by ThingPark catalogs to comply with regional regulations (allowed frequency range, duty cycle, LBT, dwell time, TxPower limits...)
Protocol & Device Support
- Support of all the device classes defined in LoRaWAN protocol: Class A, B, and C
- Compliant with the latest LoRaWAN specifications: LoRaWAN 1.0.3 and LoRaWAN 1.1
- Best-in-class Adaptive Data Rate algorithms, leveraging uplink macro diversity and frame repetition to optimize device performance, minimize battery consumption, and boost radio capacity.
- Downlink multicast, optimizing downlink radio capacity and supporting a variety of use cases for Class B/C devices.
- Optimized handling of the device's MAC layer, using cluster-based flexible channel plan management to maximize macro-diversity gains.
Security & Authentication
- Hardware Security Module (HSM) to securely provision the root keys of OTA devices.
- Software Security Mode (SSM) if a physical HSM is not available, allowing end-to-end encrypted transfer of application payload between the sensor and the application server.
- Integration with Secure Elements (SE).
- Access authentication based on standardized frameworks (KeyCloak).
Network Management & Monitoring
- Network supervision via alarms, supporting SNMP traps and email notifications.
- Device Manager Application to support device provisioning and monitoring.
- Network Manager Application to support base station provisioning, administration, and monitoring.
- KPI Dashboards to ease network monitoring and troubleshooting.
- A set of ThingPark Wireless applications to ease day-to-day network management activities: Network Survey (radio coverage assessment), Spectrum Analysis (RF scan and reporting to optimize frequency assignment).
Administration & Billing
- Managed Customer Networks: ability for the network subscriber to deploy their own gateways with an all-you-can-eat billing policy.
- Tailored set of administrative roles to fit within the organization of a typical Service Provider.
- Monthly Usage Details Records (UDR) generation by ThingPark back-office UDR Manager.
- Differentiated grades of service in ThingPark Connectivity Plans (Service profiles), supporting subscription classes like Platinum, Gold, Silver, and Basic.
- Token bucket to regulate traffic flow (ability to overbill overflow traffic).
- Specific billing reports for roaming traffic.
Integration & Compliance
- A rich set of metadata piggybacked with application payloads routed to application servers, with notification responses back to the server for each downlink packet transmission request.
- Off-the-shelf catalogs to simplify device and base station provisioning.
- HTTPS for tunneling interface between the core network and application servers, including security signatures (token-based).